Distributed Virtual Routing DVR
Private Cloud Director Networking Service uses Distributed Virtual Routing (DVR) as the primary mode to configure networking under the hood. This document describes DVR.
DVR configuration has the following characteristics:
Distributed Layer 3 (L3) space across all hypervisor hosts. No dedicated network nodes required.
North-South and East-West traffic is handled at each hypervisor host.
Advantages of DVR
High performance (L3 at compute node)
Single hop Floating IP (FIP) i.e. North-South traffic
East-West traffic also is routed at source
Failure domain reduced to a single compute node
Great load sharing in terms of L3 routing & DHCP servers
Easier for maintenance when it comes to re-purposing the otherwise central network node
DVR Deployment
Components in a DVR deployment are distributed as shown below.
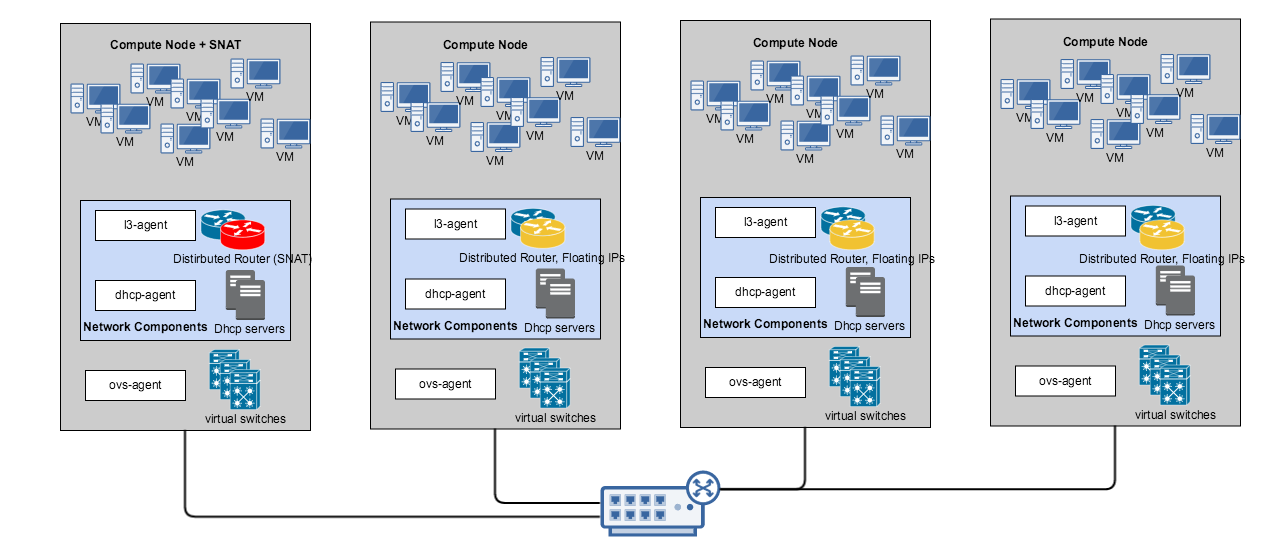
The Network components in the above picture consist of the dhcp-agent and the l3-agent. DHCP agent is responsible for managing DHCP servers for tenant networks along with DNS service while the L3 agent is responsible for routing i.e. cross networks both east-west and north-south traffic. You can assign one or more nodes to run SNAT. VMs without Floating IPs will connect external to the cloud through this SNAT service node. VMs with floating IPs however will directly communicate external to the cloud from the host/server it is running in.
Following table lists the key characteristics of DVR:
Feature
Feature Detail
Distributed Virtual Routing - L3
DHCP server
Setup
On any hypervisor. User has the control to choose which hypervisors host DHCP servers. This is scalable to 'N' where N is the number of hypervisors
Failure Domain
Active-Active
Failover
Moves to another hypervisor/node with DHCP service enabled assuming there are > 2
L3 or IP Routing
Setup
On all hypervisors for East West traffic and on SNAT enabled hypervisors for North South traffic.
SNAT
On a particular hypervisor. Load balanced to the hypervisors enabled with SNAT
Floating / Elastic IPs
On the specific hypervisor where VM runs.
North-South traffic flow
SNAT through SNAT hypervisor but when using FIP, directly through hypervisor running the VM.
East-West traffic flow
Directly at hypervisor.
Redundancy
Active-active only makes sense for SNAT. (In our roadmap)
Failure Domain
Loss of hypervisor alone. If hypervisor running SNAT, loss of SNAT till failover.
Failover
SNAT router failover to other hypervisor after timeout.
IP usage
External IPs
1 for external n/w gateway interface per L3 virtual router (SNAT), 1 each for FIP gateway/namespace (=no. of hypervisors) + 1 FIP per VM.
Internal IPs
2 per tenant network per router (1 for SNAT/ 1 for Gateway)
Last updated
Was this helpful?
